The indiscriminate attack struck hundreds of thousands of computers worldwide Friday by exploiting known vulnerabilities in older Microsoft computer operating systems.
Microsoft's president and chief legal officer Brad Smith said the US National Security Agency developed the original code used in the attack, which later leaked in a document dump.
The admission was leaped on by Putin.
"Microsoft's leadership stated this directly, they said the source of the virus was the special services of the United States," the Russian leader said on the sidelines of a summit in Beijing.
"A genie let out of a bottle of this kind, especially created by secret services, can then cause damage to its authors and creators."
Russia has recently been accused of cyber meddling in several countries, but Putin said they had nothing to do with the attack.
Tom Bossert, President Donald Trump's top cyber and homeland security adviser denied that the US was to blame.
"This was not a tool developed by the NSA to hold ransom data," he said, noting that no US government systems had been hit.
"This is a global attack," he added.
Microsoft's Smith earlier said he hoped the attacks would serve as "a wake-up call", warning governments against stockpiling code that could be misused if it fell into the wrong hands.
Vulnerabilities should be pointed out to manufacturers, he said.
"An equivalent scenario with conventional weapons would be the US military having some of its Tomahawk missiles stolen," Smith wrote.
There had been concern that Monday's start of the working week would see an upsurge in attacks.
But the cross-border police agency Europol said the situation was "stable", after attacks that struck computers in British hospital wards, European car factories and Russian banks.
"The number of victims appears not to have gone up," a senior spokesman for Europol, Jan Op Gen Oorth, told AFP.
But according to Michel Van Den Berghe, director of telecom group Orange's cyber security arm, a "second wave" is to be expected.
"Loads of people will use the original to generate variations... to recreate the panic and try to get some money for themselves," he said.
WATCH: Dan Tehan on cyber security
Telecoms and carmaking hit
US package delivery giant FedEx, Spanish telecoms giant Telefonica and Germany's Deutsche Bahn rail network were among those hit. The attackers demanded money to unblock their computers.
In China, "hundreds of thousands" of computers were affected, including petrol stations, cash machines and universities, according to Qihoo 360, one of the country's largest providers of antivirus software.
Russia said its banking and railway systems were targeted.
A fifth of regional hospital associations in Britain's National Health Service were affected and several still had to cancel appointments on Monday.
French carmaker Renault shut its Douai plant -- one of its biggest sites, employing 5,500 people -- on Monday as systems were upgraded.
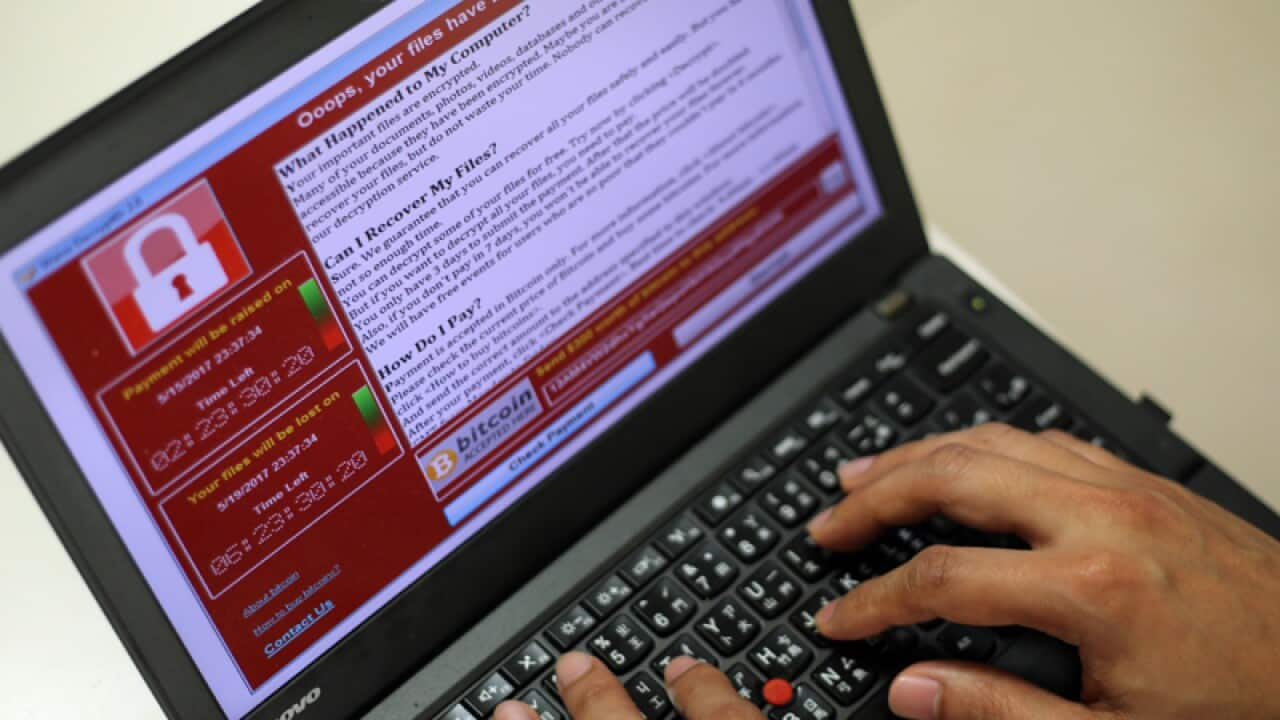
'Ooops' message, $300 ransom
The attack blocks computers and puts up images on victims' screens demanding payment of $300 (275 euros) in the virtual currency Bitcoin, saying: "Ooops, your files have been encrypted!"
Payment is demanded within three days or the price is doubled, and if none is received within seven days the locked files will be deleted, according to the screen message.
Bitcoin, the world's most-used virtual currency, allows anonymous transactions via heavily encrypted codes.
Experts and governments alike warn against ceding to the demands and few victims so far had been paying up.
Security firm Digital Shadows said on Sunday that transactions totalling $32,000 had taken place through Bitcoin addresses used by the ransomware.
A hacking group called Shadow Brokers released the malware in April, claiming to have discovered the flaw from the NSA, according to researchers at the Moscow-based computer security firm Kaspersky Lab.
The attack is unique, according to Europol, because it combines ransomware with a worm function, meaning once one machine is infected, the entire internal network is scanned and other vulnerable machines are infected.
'Significant' political fallout
Although the economic fallout is still unknown, the political fallout "will be significant" according to the Eurasia consultancy.
As well as Russia, China and India have blamed the US government for developing the original code.
It also predicted a review in the United States about when to inform software vendors of vulnerabilities in their systems and increased funding to ensure timely patches to protect computer systems.